You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Norway Norway - Arjen Kamphuis, 47, Dutch citizen, Bodø, 20 Aug 2018
- Thread starter cybervampira
- Start date
- Status
- Not open for further replies.
The phone could also travel by bus and train between Bråstein and Ualand, and I also think signals from a boat that goes along the coast would be picked up by these base stations as they all are close to the sea.
Negative. Ship reception scenario would not be possible without the use of additional enhancement extentions to boost the range of the phone.
Cave
ZaZara
AstraZaZara
- Joined
- Jan 31, 2014
- Messages
- 8,421
- Reaction score
- 17,992
the post i was looking for i could not find in this forum, just went through my posts because i questioned it, ill search some other forums..
On this forum you will find that the tent with stuff in it was ruled out.
Family and friends,
Our research has come up with a possible type of dual sim phone in use by Arjen.
Question to family and friends: does anyone of you recognise this type of phone as possible phone that Arjen might be using?

From model of phone we first can check upon possible technical connection types like
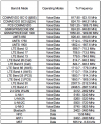
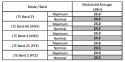
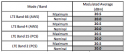

Hope you understand why model/mark is important in order to perform a rough calculation against the given cell towers.


(The above info is just an example of type of info that is used in order to predict possible location of bearer of cell phone...)
Cave
Our research has come up with a possible type of dual sim phone in use by Arjen.
Question to family and friends: does anyone of you recognise this type of phone as possible phone that Arjen might be using?

From model of phone we first can check upon possible technical connection types like




Hope you understand why model/mark is important in order to perform a rough calculation against the given cell towers.
(The above info is just an example of type of info that is used in order to predict possible location of bearer of cell phone...)
Cave
Attachments
Can you or someone else explain sim cards and pin codes and how officials might know? Is there a way criminals can fake pin code or erase it somehow?
The type of lock that you refer to as pin can either be a simlock (provider) or a personal pin (to prevent misuse of the phone and keep phone in a semi-locked station, only enabeling emergency calls.
Basicly Wikipedia covers all the basics at the page SIM lock - Wikipedia, where this SIM lock is usally referred as a methode to enforce that a customer cannot use a certain phone that he bought as package with provider 1 with a simcard of provider 2.
SIM card contains:
- A unique serial number (ICCID)
- The international mobile subscriber identity (IMSI)
- The security authentication and ciphering information
- Temporary information related to the local network
- A list of the services the user has access to
- Two passwords: a personal identification number (PIN) for ordinary use and a personal unblocking code (PUK).
However, Karsten Nohl, the founder of Security Research Labs in Berlin, says he has found a flaw in the encryption technology used in some SIM cards. This vulnerability could enable a hijacker to take control of a person’s phone. The encryption is used to disguise the SIM card (the unique serial number). Click here to learn more : https://srlabs.de/sim-card-workshope-ohm2013/
The personal code someone has to enter is not a 100% safe option (and Arjen must have know that).
The flaw allows someone to take control of the phone via SMS (short text message) and allows them to install malicious software, obtain personal information, listen to our calls and even make purchases. The problem is even more serious, because there are banking applications, games and other programs and sites that validate accounts via SMS. With this information in hand, there is no knowing how extensive the damage can be, once a SIM card has been hijacked. While most carriers have adopted a stronger encryption method, called Triple DES, there are a significant number of cards still vulnerable.
Given the fact that the above info is considered 'general knowledge' for the realm of work Arjen does, I would think that Arjen would have had some other type of operating system installed and he would have likely had an app installed to neutralize any attempt for hacking his phone or SIM.
Cave
Last edited:
Thanks I should have thought of Wiki
Thanks I should have thought of Wiki
No problem at all. I have expanded the answer in order to answer the question if your PIN is a 100% safe methode for preventing others from using your phone.
Short answer is: No. Of course a PIN from a simcard (not to be mistaken with a PIN on your phone) will prevent any regular users from being able to make regular calls or use the dataconnection of our phone (when phone was in fully lockdown and power-off position). As soon as people with more skills and more tools appear next to your phone, consider no current standard phone manufacturing solution as being 100% unbreakable.
Cave
Also, Cave, the police discuss it being turned on but as we have all learned from Arjen's you tube presentation the phone can be tracked when it is not on. Was it in a faraday cage of sorts before it pinged those three towers in the South or are police limited in their tracking informaton?
https://files.gendo.ch/Books/InfoSec_for_Journalists_V1.1.pdf
by Silkie Carlo and Arjen Kamphuis
Chapter 7: Phones & Voice/Video Calls Over
Internet
Mobile security
Many of us find our smart phones to be of great importance and
value in our everyday lives and work. The benefits of being
constantly connected to our email accounts, web browsers, social
media, calendars, and also having easy access to a high quality
camera and voice recorder, do indeed make them valuable tools.
However, they are not feasibly securable tools.
The only serious solution for information security with mobile
phones is to use burner phones, with diligence and caution.
Phone risks:
Automatic logging of your current/past locations
Automatic collection of metadata, i.e. the phone number and
location of every caller; unique serial numbers of phones
involved; time and duration of call; telephone calling card
numbers
Theft and loss of data
Remotely accessing data when phone connects to public Wi-Fi
Remotely accessing all data at any point the phone is on
Phone/voicemail tapping, intercepting, or recording
Covert remote automation of microphone to record audio
Covert remote automation of camera to capture images
Dragnet phone surveillance
All phones leak an enormous amount of information about us to
intelligence agencies, and we know from the Snowden revelations
that programs collecting the full audio of every single call within a
nation are, at the very least, already in place and being trialled in
some countries. This type of surveillance is extremely dangerous for
democracy, let alone journalism, and may permit the most invasive
‘retroactive’ investigation of individuals who become of interest to
intelligence agencies at some point in the future.
Therefore, it is worth using any phone with this in mind, whether
you, your sources or colleagues may be targets of intelligence
agencies now, or years in the future. They are not secure
communication devices, so consider carefully how you want to use
them.
Targeted phone surveillance
I
nformation Security for Journalists – November 2014: Version 1.1 – page
80
Low risk
At a low risk level, the threat is mainly physical – someone gaining
access to the handset. If this happens, even a fairly unsophisticated
hacker/the police can crack your password (if you use a password
lock) so this only provides minimal protection. If you are at a low risk
level, be sure to back up your data and stream or send any video or
audio being recorded on the device to a secure storage cloud as
soon as possible.
You can also use applications to track your device, should it be
stolen. For iPhone, for instance, Apple offer a free app called ‘Find
my iPhone’ which tells you the current location of your phone.
Another free anti-theft app is ‘Prey’ which, once you report the
phone as stolen, will record not only the current location of the
phone, but any other locations of the phone registered since you
reported it stolen.
Medium risk
At a medium risk level, you may encounter an adversary trying to
gain access to your data, not just physically, but remotely. When
you connect a phone to a public Wi-Fi connection, for example, a
fairly unsophisticated hacker can intercept lots of information about
you and connected accounts such as email and social media.
Therefore, at a medium risk level, you may already be thinking
about avoiding a smart phone as a work tool, or at least guarding it
closely, closing applications after use, turning off Wi-Fi in public, and
using flight mode when you don’t need to be connected.
A note about smart phones: the vulnerabilities of smart
phones are numerous, with some existing in the hardware,
and they are not fixable. You can use open source software on
smart phones, and even applications for encrypted chat.
However, as we discovered in ‘Protecting the System’, when
hardware is vulnerable, the software cannot provide you with
real security. Therefore, we will not discuss such apps for the
purpose of this guide.
As the recent phone hacking scandal in the UK demonstrated,
unsophisticated hackers working for unethical journalists were able
to listen in on people’s voicemail. Private investigators often also
have the ability to ‘phone tap’ (i.e. eavesdrop) not only voicemail
but general phone calls made and received by a number. Therefore,
you should think before you discuss anything sensitive on your
(mobile or indeed landline) phone.
High risk
At a high risk level, a phone basically
is
your adversary. At the very
least, it locks your location and all associated metadata with the
device is in the hands of a Five Eyes intelligence agency. At worst, it
can be used to covertly collect the content of all of your phone calls,
let alone all other data on the phone, and can covertly automate
your microphone and camera to record audio and images (if it has a
camera) too. This type of phone surveillance is very easy and
basically comes at zero-cost to Five Eyes intelligence agencies, so
you may not necessarily be an important target for them to justify
this type of privacy invasion.
The only serious secure way of using phone communications is to
use burner phones.
Ideally, your burner phone and regular phone will never both be
emitting signals, since (if you are a target), your regular phone may
pick up on the signal of the burner phone, making that a target too.
Before you use a burner, make sure the phone usually associated
with you (e.g. your smart phone) is not emitting signals. Switching
the phone to flight mode, removing the battery (don’t bother trying
to do this to the iPhone), and turning it off is good but is not enough.
Do all of these things and then put it in a Faraday cage – popular
solutions are biscuit tins, some fridges, or even a stainless steel
cocktail shaker! The phone has to be completely sealed in metal
(check it is working by trying to call the phone). It is a good idea to
find and carry a small tin around with you to put your phone in, and
in an important meeting, make sure all attending have done the
same (a larger biscuit tin works well here).
A burner phone is a cheap, cash-bought, throwaway, low-tech
phone, with a prepaid SIM card not registered to you, to be used
only for specific purposes. It can be hard, in some countries, to buy
a SIM card without registering it with your personal details.
Therefore, buying second-hand, or having a contact that can obtain
such SIM cards, is ideal.
After some use of the phone, the phone may become associated
with you and attract surveillance, at which point you should destroy
it and use a new one. Changing the SIM card is not enough – each
phone handset also has an IMEI (International Mobile Equipment
Identity) number that identifies the phone. If the SIM has been
identified as being yours, the IMEI will be too – so you will need to
destroy the phone.
Due to intelligence agencies rolling out full audio recording of all
phone calls, let alone the ease with which they can record a target’s
I
nformation Security for Journalists – November 2014: Version 1.1 – page
82
phone calls, you should avoid sharing particularly sensitive
information - even on a burner phone.
by Silkie Carlo and Arjen Kamphuis
Chapter 7: Phones & Voice/Video Calls Over
Internet
Mobile security
Many of us find our smart phones to be of great importance and
value in our everyday lives and work. The benefits of being
constantly connected to our email accounts, web browsers, social
media, calendars, and also having easy access to a high quality
camera and voice recorder, do indeed make them valuable tools.
However, they are not feasibly securable tools.
The only serious solution for information security with mobile
phones is to use burner phones, with diligence and caution.
Phone risks:
Automatic logging of your current/past locations
Automatic collection of metadata, i.e. the phone number and
location of every caller; unique serial numbers of phones
involved; time and duration of call; telephone calling card
numbers
Theft and loss of data
Remotely accessing data when phone connects to public Wi-Fi
Remotely accessing all data at any point the phone is on
Phone/voicemail tapping, intercepting, or recording
Covert remote automation of microphone to record audio
Covert remote automation of camera to capture images
Dragnet phone surveillance
All phones leak an enormous amount of information about us to
intelligence agencies, and we know from the Snowden revelations
that programs collecting the full audio of every single call within a
nation are, at the very least, already in place and being trialled in
some countries. This type of surveillance is extremely dangerous for
democracy, let alone journalism, and may permit the most invasive
‘retroactive’ investigation of individuals who become of interest to
intelligence agencies at some point in the future.
Therefore, it is worth using any phone with this in mind, whether
you, your sources or colleagues may be targets of intelligence
agencies now, or years in the future. They are not secure
communication devices, so consider carefully how you want to use
them.
Targeted phone surveillance
I
nformation Security for Journalists – November 2014: Version 1.1 – page
80
Low risk
At a low risk level, the threat is mainly physical – someone gaining
access to the handset. If this happens, even a fairly unsophisticated
hacker/the police can crack your password (if you use a password
lock) so this only provides minimal protection. If you are at a low risk
level, be sure to back up your data and stream or send any video or
audio being recorded on the device to a secure storage cloud as
soon as possible.
You can also use applications to track your device, should it be
stolen. For iPhone, for instance, Apple offer a free app called ‘Find
my iPhone’ which tells you the current location of your phone.
Another free anti-theft app is ‘Prey’ which, once you report the
phone as stolen, will record not only the current location of the
phone, but any other locations of the phone registered since you
reported it stolen.
Medium risk
At a medium risk level, you may encounter an adversary trying to
gain access to your data, not just physically, but remotely. When
you connect a phone to a public Wi-Fi connection, for example, a
fairly unsophisticated hacker can intercept lots of information about
you and connected accounts such as email and social media.
Therefore, at a medium risk level, you may already be thinking
about avoiding a smart phone as a work tool, or at least guarding it
closely, closing applications after use, turning off Wi-Fi in public, and
using flight mode when you don’t need to be connected.
A note about smart phones: the vulnerabilities of smart
phones are numerous, with some existing in the hardware,
and they are not fixable. You can use open source software on
smart phones, and even applications for encrypted chat.
However, as we discovered in ‘Protecting the System’, when
hardware is vulnerable, the software cannot provide you with
real security. Therefore, we will not discuss such apps for the
purpose of this guide.
As the recent phone hacking scandal in the UK demonstrated,
unsophisticated hackers working for unethical journalists were able
to listen in on people’s voicemail. Private investigators often also
have the ability to ‘phone tap’ (i.e. eavesdrop) not only voicemail
but general phone calls made and received by a number. Therefore,
you should think before you discuss anything sensitive on your
(mobile or indeed landline) phone.
High risk
At a high risk level, a phone basically
is
your adversary. At the very
least, it locks your location and all associated metadata with the
device is in the hands of a Five Eyes intelligence agency. At worst, it
can be used to covertly collect the content of all of your phone calls,
let alone all other data on the phone, and can covertly automate
your microphone and camera to record audio and images (if it has a
camera) too. This type of phone surveillance is very easy and
basically comes at zero-cost to Five Eyes intelligence agencies, so
you may not necessarily be an important target for them to justify
this type of privacy invasion.
The only serious secure way of using phone communications is to
use burner phones.
Ideally, your burner phone and regular phone will never both be
emitting signals, since (if you are a target), your regular phone may
pick up on the signal of the burner phone, making that a target too.
Before you use a burner, make sure the phone usually associated
with you (e.g. your smart phone) is not emitting signals. Switching
the phone to flight mode, removing the battery (don’t bother trying
to do this to the iPhone), and turning it off is good but is not enough.
Do all of these things and then put it in a Faraday cage – popular
solutions are biscuit tins, some fridges, or even a stainless steel
cocktail shaker! The phone has to be completely sealed in metal
(check it is working by trying to call the phone). It is a good idea to
find and carry a small tin around with you to put your phone in, and
in an important meeting, make sure all attending have done the
same (a larger biscuit tin works well here).
A burner phone is a cheap, cash-bought, throwaway, low-tech
phone, with a prepaid SIM card not registered to you, to be used
only for specific purposes. It can be hard, in some countries, to buy
a SIM card without registering it with your personal details.
Therefore, buying second-hand, or having a contact that can obtain
such SIM cards, is ideal.
After some use of the phone, the phone may become associated
with you and attract surveillance, at which point you should destroy
it and use a new one. Changing the SIM card is not enough – each
phone handset also has an IMEI (International Mobile Equipment
Identity) number that identifies the phone. If the SIM has been
identified as being yours, the IMEI will be too – so you will need to
destroy the phone.
Due to intelligence agencies rolling out full audio recording of all
phone calls, let alone the ease with which they can record a target’s
I
nformation Security for Journalists – November 2014: Version 1.1 – page
82
phone calls, you should avoid sharing particularly sensitive
information - even on a burner phone.
worldwatcher
Well-Known Member
- Joined
- Jan 1, 2010
- Messages
- 1,955
- Reaction score
- 10,517
Kayak:
Ten days later, over a thousand kilometers to the south, his telephone is switched on briefly and at the beginning of this month a collapsible kayak is found near Bodø. His identity papers were in there, Van de Leest said earlier in another newspaper. Now she says: "The police have asked me not to give too many details."
That kayak raises questions at Van de Leest. "He did not particularly like kayaking," she says. "And he had not told anyone that he had a kayak, that is separate too." In addition, the thing, based on the images, was rather rickety put together. "That is remarkable, because we do not know Arjen like that, he would be proud to put the kayak together, which is something that keeps on haunting me." The police have now stopped searching in the area where the canoe was found.
Alleen maar mist rond vermissing Kamphuis | TROUW
I do not know that Arjens ID was found in the kayak...did I miss something?
Seems odd that if several days before founding this kayak,it was pulled on shore by someone and yet his ID was found it...
Strange...very strange..
Ten days later, over a thousand kilometers to the south, his telephone is switched on briefly and at the beginning of this month a collapsible kayak is found near Bodø. His identity papers were in there, Van de Leest said earlier in another newspaper. Now she says: "The police have asked me not to give too many details."
That kayak raises questions at Van de Leest. "He did not particularly like kayaking," she says. "And he had not told anyone that he had a kayak, that is separate too." In addition, the thing, based on the images, was rather rickety put together. "That is remarkable, because we do not know Arjen like that, he would be proud to put the kayak together, which is something that keeps on haunting me." The police have now stopped searching in the area where the canoe was found.
Alleen maar mist rond vermissing Kamphuis | TROUW
I do not know that Arjens ID was found in the kayak...did I miss something?
Seems odd that if several days before founding this kayak,it was pulled on shore by someone and yet his ID was found it...
Strange...very strange..
Chiatos
Well-Known Member
- Joined
- Aug 29, 2014
- Messages
- 1,902
- Reaction score
- 6,165
2G/3G/4G are NOT used to transmit or receive sms?In order to perform an analysis of possible locations we would need to know which was the exact application that was used on which basis it was said that the message was 'received'.
Knowing the mark of the phone and name of the application would give insight to analysis which transmission type (2G/3G/4G) is likely to have been used.
The ranges for 2G/3G/4G are all different. Knowing the application and phone type would give insight in transmission type and would enable us to make a full map where coverage of that type of transmission would be feasible (= where bearer of phone could have performed that type of transmission).
Family and or friends of Arjen, additional information on Arjens phones and type of communication apps is essential in order to perform calculations and analyses of connection possibilities.
If info is considered confidential, please consider contacting us privately.
Since Ancilla told in interviews about her sending messages to Arjan (6/8 or 7/8 and 9/8), Ancilla would be able to tell which application was used.
Also name of original provider would be helpfull (can be found in administration of Arjen, billing info).
If info regarding the type of phone is simply not available among family and friend, please consider making a schedule to screen all videos where Arjen appears for any remarks he might have made during such an appearance about the type of phone he used.
Cave
Family of Arjen
Active Member
- Joined
- Sep 23, 2018
- Messages
- 16
- Reaction score
- 119
Arjen has no driver's license.Did he drive? Would he rent a car? Would be easier as a local to get some idea how he could travel around...
worldwatcher
Well-Known Member
- Joined
- Jan 1, 2010
- Messages
- 1,955
- Reaction score
- 10,517
So the drivers license/ID of that can be defentitly ruled out.Arjen has no driver's license.
@Family of Arjen - thank you! It will give us locals a better picture how he could travel around. Mostly with bus and train then..
Family of Arjen
Active Member
- Joined
- Sep 23, 2018
- Messages
- 16
- Reaction score
- 119
Do you have a centralized list of open questions and findings?
If so, can you consider sharing this list in order to Tarjei and me so we can be working with you in order to visualize all other facts and findings and be sure not to overlook a particular issue?
If there are items that are know, but that you do not want to be public, that is no problem and we can generate and maintain private/confidential information maps just for family/relative/close friends purposes as well.
Cave
All these questions are the same as asked by the members of this forum. In short: what has the police done to find more people that has seen Arjen in Bodo (till now one person). When and where exactly were the pings of his telephone in and around Bodo, and what do they say about what he was doing. The same for Fauske and Rognan (kayak, baggage, telephone, people). And what about the pings in the south of Norway, and tips from different places.
May more about Arjens telephone(s) later.
worldwatcher
Well-Known Member
- Joined
- Jan 1, 2010
- Messages
- 1,955
- Reaction score
- 10,517
Searched for more options due to rental transport
In the beginning there was a mention of a bike
Found this,can not read it all,because have to leave for work but will try to upload it for later
Ohhh too large for upload (pdf) but it all about public transport,ferry,rentals
Nord-Norge - Den offisielle nettsiden for unike opplevelser nord i Norge>sites>files
NOORD-Noorwegen-Nordnosk-reiseliv
In the beginning there was a mention of a bike
Found this,can not read it all,because have to leave for work but will try to upload it for later
Ohhh too large for upload (pdf) but it all about public transport,ferry,rentals
Nord-Norge - Den offisielle nettsiden for unike opplevelser nord i Norge>sites>files
NOORD-Noorwegen-Nordnosk-reiseliv
The articles about the paddle in No. papers are mainly from the 17th of Sept. and says that the police got a message from a privat person (whom found it in the same area as the kayak) a few days earlier.That map by Tarjei and Caveman is great!
One question: the paddle was found on Sept. 1st? According to Rolien Creton / NOS it was found on Sept. 17th?
"200m verderop werd gisteren de bijbehorende peddel gevonden."
Also, Cave, the police discuss it being turned on but as we have all learned from Arjen's you tube presentation the phone can be tracked when it is not on. Was it in a faraday cage of sorts before it pinged those three towers in the South or are police limited in their tracking informaton?
I know for 100% fact that Arjen had possession of special bags/pouches with RFID shielding for transporting equipment (laptops, disks, phones, cards etc).
Whether he took these bags with him during his holiday is not known. If he would place his phone or phones in one of those RFID shielding bags, these phone or phones would be fully 'shielded' from making contact with celltowers.
As soon as you take your phone from such a bag, reception is restored.
Cave
Chiatos
Well-Known Member
- Joined
- Aug 29, 2014
- Messages
- 1,902
- Reaction score
- 6,165
Exactly. That's why I'm asking why Tarjei+Cave's map says September 1st.The articles about the paddle in No. papers are mainly from the 17th of Sept. and says that the police got a message from a privat person (whom found it in the same area as the kayak) a few days earlier.
I do not have the technical knowledge to discuss this, I jst dont want to clear out any possibilities before they are totally searched, this article has a map that shows coverage at sea and says the landscape has a lot to do according to coverage: WikiLeaks-medarbeider kan ha seilt utenfor Rogalands-kystenNegative. Ship reception scenario would not be possible without the use of additional enhancement extentions to boost the range of the phone.
Cave
- Status
- Not open for further replies.
DNASolves
Online statistics
- Members online
- 229
- Guests online
- 3,711
- Total visitors
- 3,940
Totals may include hidden visitors.



