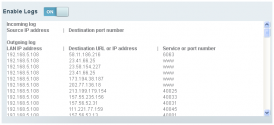
It won't, not unless someone tries to join your network. Then it will.
It's stored in the router, not at your ISP, is my understanding. We could use an expert. LE certainly has them. Most of what I know is coming from LEO's and college IT security people I know. It's not useless. If we didn't have that capacity, Bad Guys would be hacking into routers with impunity. You can go google just how many people never change the manufacturer's default name and password.
I am passing this info on because I think everyone should know that their router will record any stranger attempts to pass through your network. At least, modern routers will. I don't know for how long, but it shouldn't be a whole heckuva a lot of people.
It's very useful for catching pedophiles and child pornographers, btw.
A guy who was using a hospital based network (but parked near our house which backed onto the hospital) was captured in just this way. It was his proximity to a school that caused more than one person to call him into local PD as a possible nuisance (there every afternoon). He was using the hospital connection to upload child *advertiser censored* (not made at the school, and no pictures of local children were found). They identified him by his device number, stored in the hospital's system via router. He had not, apparently, tried to use our network, thankfully.
Apparently big institutions pay attention to traffic that is directed toward the dark web (although I don't think the provisions in place are able to keep up with the way that perps find to get around them).
SG's statements in this case state that LE told him that the girls' router was "touched" by BK's phone. That's the main point (not passing through, just "touching"). And I believe SG is accurate and I believe LE would have looked at that. For sure.
Wireless networks are less secure than wired networks. Here's how to hide your Wi-Fi network from others and what you should know about doing so.

www.makeuseof.com
//Routers constantly broadcast something called a
beacon frame, which is a transmission that contains information about the network. It includes the SSID and is meant to announce that this network exists.//
(From that article - so everyone can ponder how much they want the world to know about their own router). Emphasis is not mine, it's in the article. You can use this term to look up how it works. Here's the first result:

en.wikipedia.org